Tech Chirps
Our insightful blog offers insights, tips, success tales, and indispensable advice for perfecting your business, home, or gaming setup!
How to Re-Pair Bluetooth Devices
If your Bluetooth headphones, keyboard, speaker, or other device suddenly stops working with your phone, tablet, or computer, the most effective fix is usually to re-pair the device. Re-pairing means removing the existing connection and starting fresh.
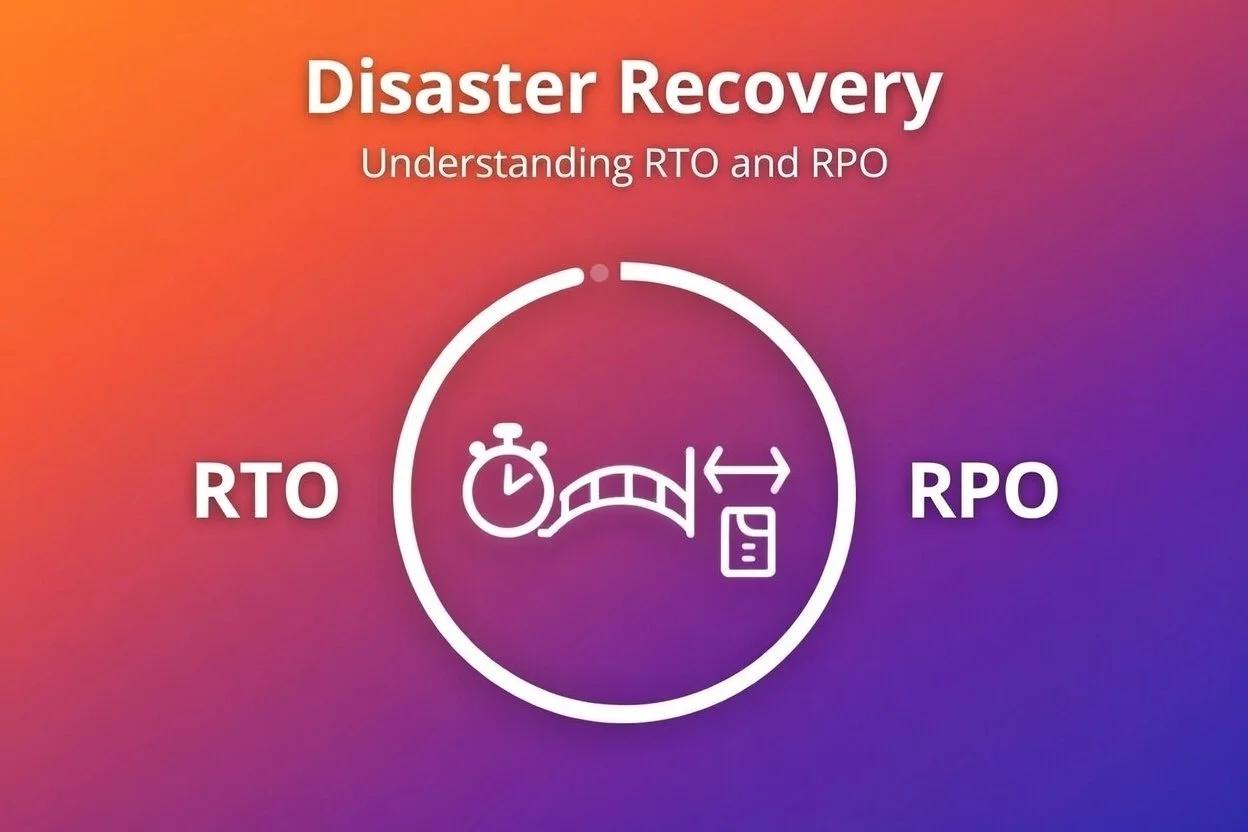
RTO and RPO in Disaster Recovery
When disaster strikes - be it a cyberattack, hardware failure, or natural event - your organisation’s ability to recover quickly and limit data loss can mean the difference between a minor hiccup and a major crisis.
Importance of Data Backups
From accidental deletions to ransomware infections, the possibility of losing critical data is very real. Data backups provide a crucial safety net - letting you restore information quickly and minimise downtime, even if your primary systems are compromised or destroyed.
Updating iOS/Android Without Issues
Keeping your smartphone’s operating system (OS) up to date is one of the easiest and most effective ways to improve speed, fix bugs, and stay secure. But many home users worry that an update might slow things down or cause something to go wrong.
Battery Draining Too Fast: What to Do
Is your phone battery draining faster than usual? Does it go flat halfway through the day - or even sooner? If so, you’re not alone. Many people on the Central Coast experience rapid battery drain on their Android or iPhone, even with minimal use.
Fixing App Crashes and Freezing
Is your smartphone acting up - apps crashing randomly, freezing in the middle of something important, or just refusing to open at all? Don’t worry. These issues are common on both Android and iPhone devices, and in most cases, they’re easy to fix.
Managing Storage: Free Up Space Easily
Running out of storage on your phone can be incredibly frustrating - especially when you’re trying to take a photo, install an app, or update your device. Fortunately, you don’t need to be tech-savvy to reclaim space and keep your phone running smoothly.
How to Force Restart Android and iOS
If your smartphone is frozen, unresponsive, or stuck on a black screen, your first instinct might be to panic or head straight to the nearest repair shop. But wait - force restarting your phone is often all it takes to get things working again.
What Causes Computers to Freeze?
Your computer freezing can be frustrating, especially when you’re in the middle of something important - like writing an email, joining a video call, or printing a document. But why does it happen? While a one-off freeze is often nothing to worry about, frequent freezing could point to deeper issues.
Types of Disaster Recovery Solutions
From ransomware to natural disasters, disruptive events can strike unexpectedly - threatening your ability to access critical data and keep essential services online. Disaster Recovery (DR) solutions come in various forms, each designed to help you restore operations and minimise downtime.
What Is Disaster Recovery?
From cyberattacks and ransomware to natural disasters and hardware failures, unplanned events can strike at any time - potentially halting critical business operations and risking data loss. Disaster recovery (DR) aims to minimise downtime, preserve essential data, and enable your organisation to resume normal function as swiftly as possible.
Detecting and Removing Malware
Is your computer acting strangely - freezing often, running slowly, or showing strange pop-ups? There’s a good chance it might be infected with malware. Malware is unwanted software designed to cause damage, steal data, or disrupt how your computer works. The good news is, detecting and removing malware can be simple, and this guide is here to walk you through it.
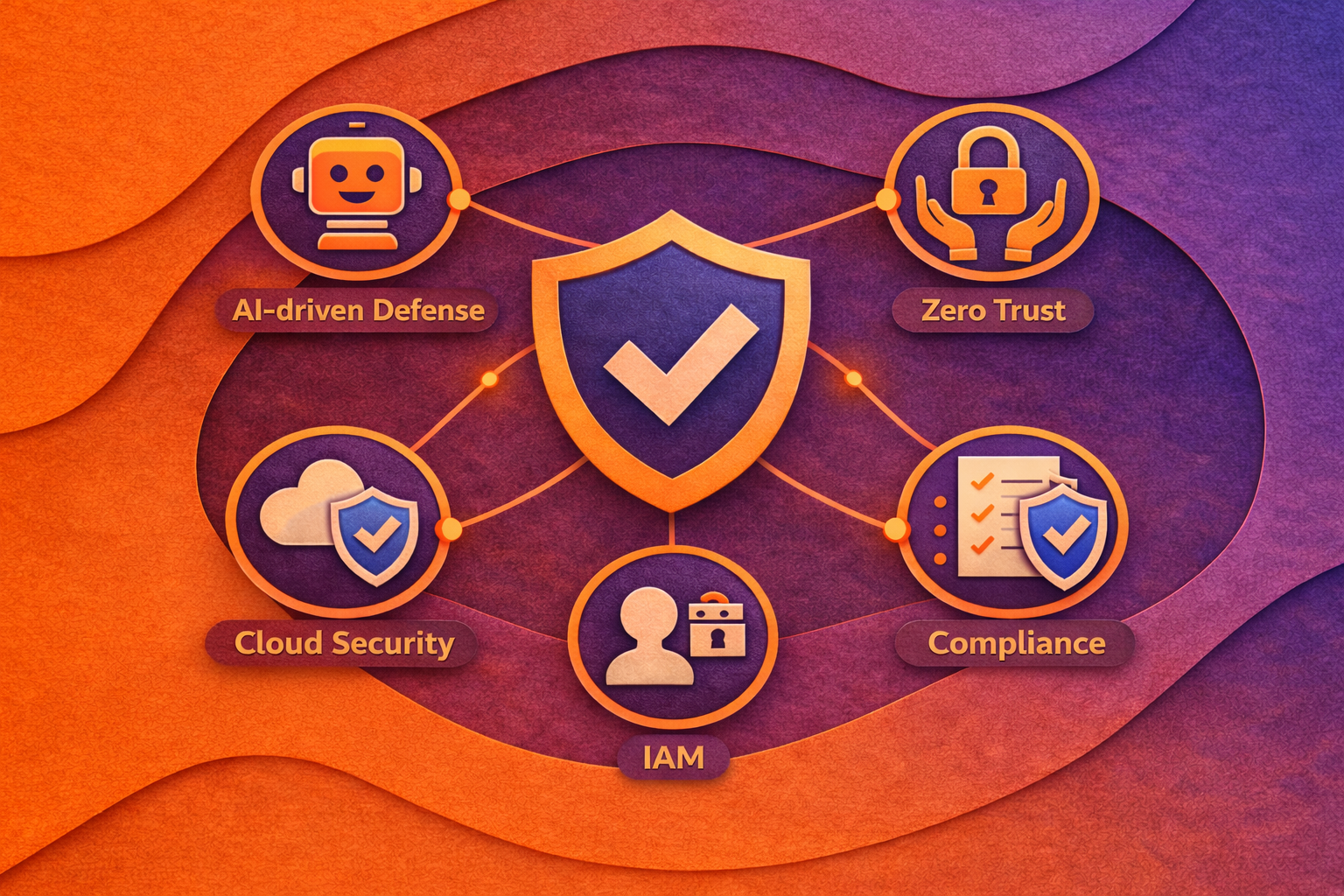
AI and Automation in Cybersecurity
In this article, we’ll explore AI and automation in cybersecurity - why they matter, what benefits they bring, and how to integrate them into an overall security strategy attuned to Australian standards.
Trends in Cybersecurity Management
In this article, we’ll explore current trends in cybersecurity management - how they’re reshaping defence strategies, what key technologies are on the rise, and how Australian standards fit into the picture.
Clearing System Cache and Temp Files
Does your computer feel slower than usual? Is it freezing more often or taking too long to load basic programs? One common cause of these issues is built-up system cache and temporary files. These files are meant to be temporary but often hang around, clogging up your computer and affecting performance over time.
Using Task Manager to Unfreeze a PC
We've all experienced it - a frozen computer that stops responding while you're browsing the internet, writing a document, or watching a video. When your PC locks up, it can feel like your only option is to restart and hope for the best. But before you hit that power button, there’s a better solution: Task Manager.
How to Boot into Safe Mode (Windows/Mac)
Is your computer freezing, crashing, or acting strange? If so, starting your computer in Safe Mode is a great way to diagnose and fix problems. Safe Mode is like a “clean version” of your operating system - it loads only the basic files and drivers needed to run, which helps identify if a background program or driver is causing trouble.
Managing Startup Programs for Faster Boot
Is your computer taking ages to start up? Do you switch it on, walk away to make a cup of tea, and it’s still not ready when you return? If so, it’s likely being slowed down by too many startup programs - apps that launch automatically when you turn your computer on.
Cybersecurity in Cloud Environments
As businesses increasingly shift data and applications to cloud platforms, securing these resources becomes a top priority. While cloud services offer flexibility and cost savings, they also create new attack surfaces and shared responsibilities.
Disk Cleanup Tools and Tips
Over time, your Windows computer or laptop builds up clutter - temporary files, system junk, outdated downloads, and unused apps. This clutter can slow down your system, take up valuable space, and even cause programs to crash. But the good news is: cleaning up your disk is simple and highly effective.